Information technology relies on humanity (at least so far). Does it work the other way around? I’ll leave this question for you to think about and will get back to the topic. Since we live in the information age, people pay money to protect the availability, integrity, and confidentiality of information. Data defense costs have increased rapidly for the past decade. Every time you need to increase security, bet it will cost some. Whether you are a company or a user. If you are an international company, chances are you can afford the dedicated network team and hardware necessary for protection. However, what budget for security is left in a nonprofit organization, small city, public school, small business, etc..? They rely on what they are given. There is very little room for research on how are they being probed from the internet. And that’s why you should know about honeypots.
What are honeypots?
In 2003, Lance Spitzner wrote a book called Honeypots: Tracking Hackers. This was one of the first books explaining and describing honeypots in detail. His definition was “a security resource whose value lies in being probed, attacked, or compromised.”
It is not a device providing services to end-users. It actually doesn’t do anything until somebody decides to communicate with it. Honeypot’s goal is to be attacked and probed. Any attempt at communication is suspicious as no regular user would request information from this device. Such attempts are monitored and stored for later analysis.
Divination of honeypots
- Types
- Honey system – a full operating system with services (ex. Windows 7)
- Honey service – a specific software or protocol function (ex. HTTP server)
- Honey token – “legitimate” data (ex. PDF file)
- Characteristics
- Deceptive (hiding/showing) – feign to be a legitimate system, software, or other entity.
- Discoverable – usually placed within the network environment.
- Interactive (low/medium/high) – high interactive is not usually used in corporate environment as alert frequency is very high. They are more likely to be used for general research.
- Monitored
- Purpose
- Research honeypot – trying to grab 0 days, attacker’s motives, and other methods.
- Production honeypot – more likely to be found within companies and their internal networks as its goal is to increase security and security awareness of a specific environment.
Deployment of honeypot
In relation to a network, a honeypot can be placed externally, internally, or in DMZ. External honeypot will detect all malicious probes. They are more likely to be research honeypots. Another type would be a production honeypot. For intruder detection, DMZ honeypot would be the right way. Characteristics have to be balanced and thought about prior to deploying a honeypot. It all depends on what goal you are trying to achieve.
List of comercial honeypots:
- Thinks Canary – low-cost software and hardware honeypots
- Cymmentria – redirects attacking attempts for detailed analyzation
- TrapX – various honeypots paired with visualization and analysis tools
List of open-source honeypots:
- Cowrie – SSH honeypot with “actual” file system
- Conpot – an industrial control system honeypot
- Dionaea – a honeypot designed to capture malware samples (written in C with an interface based on Python). Dionaea is able to identify OS with fingerprints, emulate services, collect easily exportable data and it can even reply to attacks for testing purposes.
- RDPy – a remote desktop protocol honeypot
- Open Canary – A multi-service honeypot supported by Thinkst (creators of Canary)
- Glastopf – a web app honeypot
- HoneyPress – a honeypot designed to simulate the WordPress content management system
Lots of are left in both categories.
Risk of detection
The whole purpose of the honeypot is to lure the attacker into a trap. If the “victim” (in this case attacker) recognizes there is a trap, he can easily avoid further interaction or even flood the system with fake and misleading data. There are a few methods on how to detect a honeypot. Low interaction systems are the most vulnerable to detection due to unique characteristics (fingerprints).
Running a honeypot is an extra layer of protection and can be a source of valuable information. If deployed wrong, it can also cause more harm than good.
Running public honeypot T-pot
If you want to try it yourself, you can deploy an all-in-one Tpot – multi-honeypot solution. You can find everything about the project here.
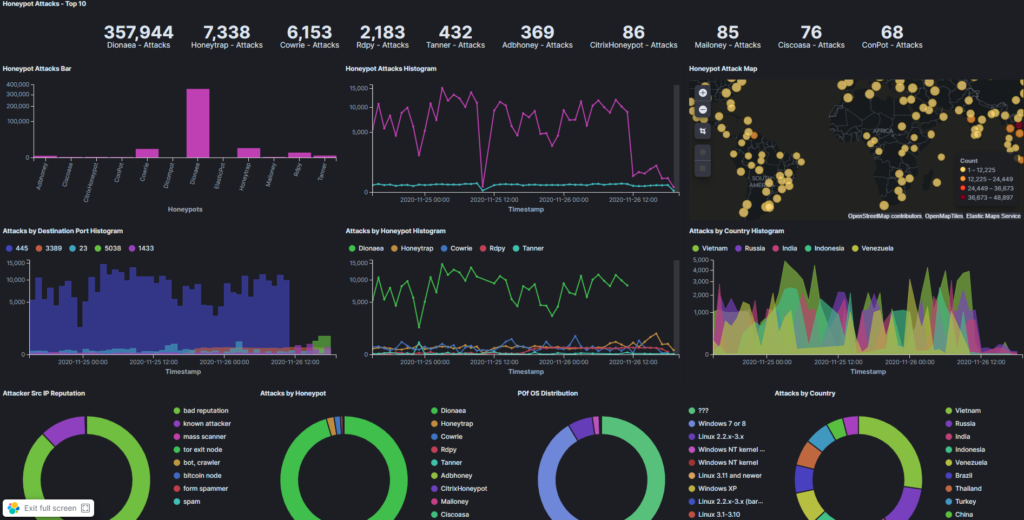
This will give you an idea, how many attacks are ongoing in real-time. Once deployed, it will immediately start counting incoming probes. In 30 seconds, I’ve received over 100 attacks. After 48 hours, the number of incoming attacks was almost 400k.